“Is our company safe from cyber-attacks?”
If you’re a CEO or board member, this question has likely crossed your mind. And if it hasn’t, it should.
Cybersecurity isn’t just about protecting data anymore. It’s about safeguarding your entire business operation, your reputation, and your bottom line.
Every day, companies like yours face cyber threats that could:
- Halt operations
- Leak sensitive information
- Drain finances
- Damage customer trust
The twist? You might not even know you’re under attack until it’s too late.
This isn’t fearmongering. It’s the reality of doing business in a digital world. But here’s the good news: with the right approach, your management team can mitigate cybersecurity risks more effectively.
Let’s explore how.
The Cybersecurity Paradox: More Digital, More Vulnerable
Picture your organization as a bustling city. As it grows and thrives, attracting more residents (customers) and building new infrastructure (digital systems), it also becomes a more attractive target for criminals. The same digital transformation that powers your growth also expands your attack surface.
Consider these sobering realities:
- Cyber threats are evolving at an alarming rate, with AI-enabled attacks on the horizon.
- The potential impacts are devastating loss of sensitive information, operational disruption, and financial loss.
- Threat actors range from profit-driven criminals to state-sponsored entities and even insiders.
The Million-Dollar Question
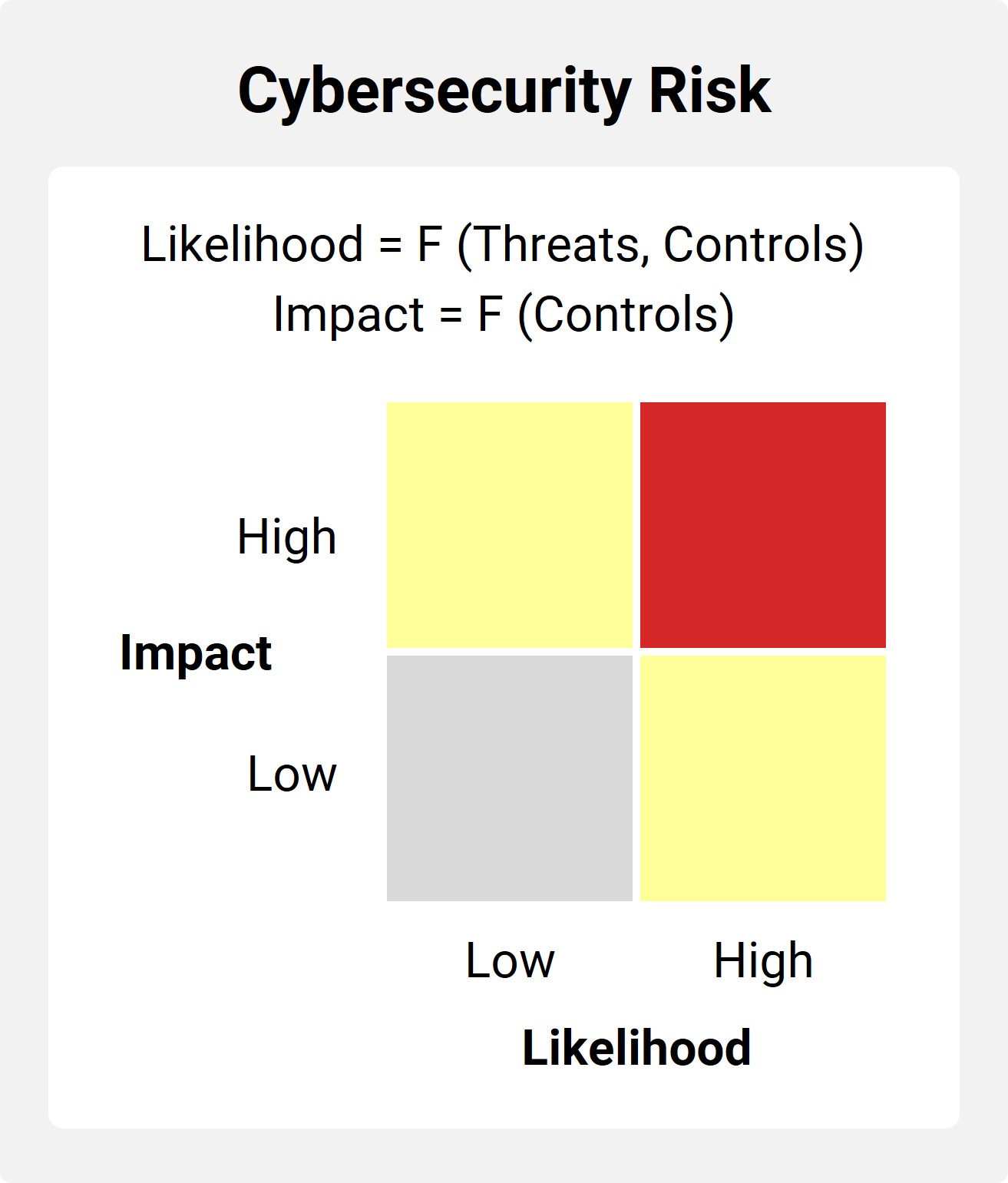
As a leader, you’re probably asking: “What’s the likelihood of a cybersecurity incident, and what could be the impact on our organization?”
The answer lies in understanding two critical factors:
- Cyber Threat Activity: The external forces that are working against you.
- Effectiveness of Your Cyber Controls: Your city’s defense system.
The High Stakes of Cybersecurity Incidents
Cybersecurity breaches can have far-reaching consequences. Here are the three main impacts that keep business and cybersecurity leaders awake at night:
- Loss of Sensitive Information:
- This includes customer data, financial records, HR information, M&A plans, and trade secrets.
- The exposure of such information can cause significant, sometimes irreparable, damage to your company.
- Operational Disruption:
- In our digital age, a targeted cyber-attack can completely halt your business operations.
- This is particularly concerning for critical infrastructure providers like hospitals, utilities, telecom companies, banks, and government agencies.
- Financial Loss:
- Cyber criminals are increasingly focused on theft, fraud, and extortion.
- For example, in 2016, hackers stole $81 million from the Bank of Bangladesh in just hours, exploiting the SWIFT banking system.
Beyond these direct impacts, a cyber incident can also result in significant brand and reputational damage, potentially leading to long-term loss of customer trust and business value.
Understanding the Threat Landscape
Who Are the Threat Actors?
Cybersecurity threats come from various sources, each with different motivations:
- Criminals: Profit-driven, using fraud, theft, and extortion.
- State-Sponsored Actors: Seeking advantages for their nations.
- Hacktivists: Primarily motivated by propaganda.
- Insiders: Can be accidental (e.g., introducing malware) or deliberate (e.g., stealing information).
- Thrill Seekers: Exploiting vulnerabilities to demonstrate their skills.
Common Types of Cyber Attacks
Cyber attackers use a wide range of tactics, including:
- Malware: Malicious software that alters system functions without consent (e.g., viruses, worms, spyware).
- Ransomware: Software that blocks access to systems until a ransom is paid.
- Denial of Service (DDoS): Overwhelming systems to make them unavailable.
- Exploit Kits: Software that identifies and exploits vulnerabilities to execute malicious code.
- Social Engineering: Using deception or manipulation to exploit human vulnerabilities (e.g., phishing, scams).
Building Your Cyber Fortress
There’s no single solution to protect against all cybersecurity threats. Effective defense requires careful planning and execution:
- Leadership: A Chief Information Security Officer (CISO) leads a team of security architects, operators, and cyber intelligence experts.
- Cross-Functional Collaboration: The security team must work closely with business units, functions and external stakeholders.
- External Partnerships: Collaboration with law enforcement, government agencies, and strategic suppliers is crucial.
- Comprehensive Approach: Defense strategies should address people, processes, and technological aspects of cybersecurity.
- Continuous Adaptation: Regular updates to security measures are necessary to keep pace with evolving threats.
Organizational Capabilities and Stakeholders
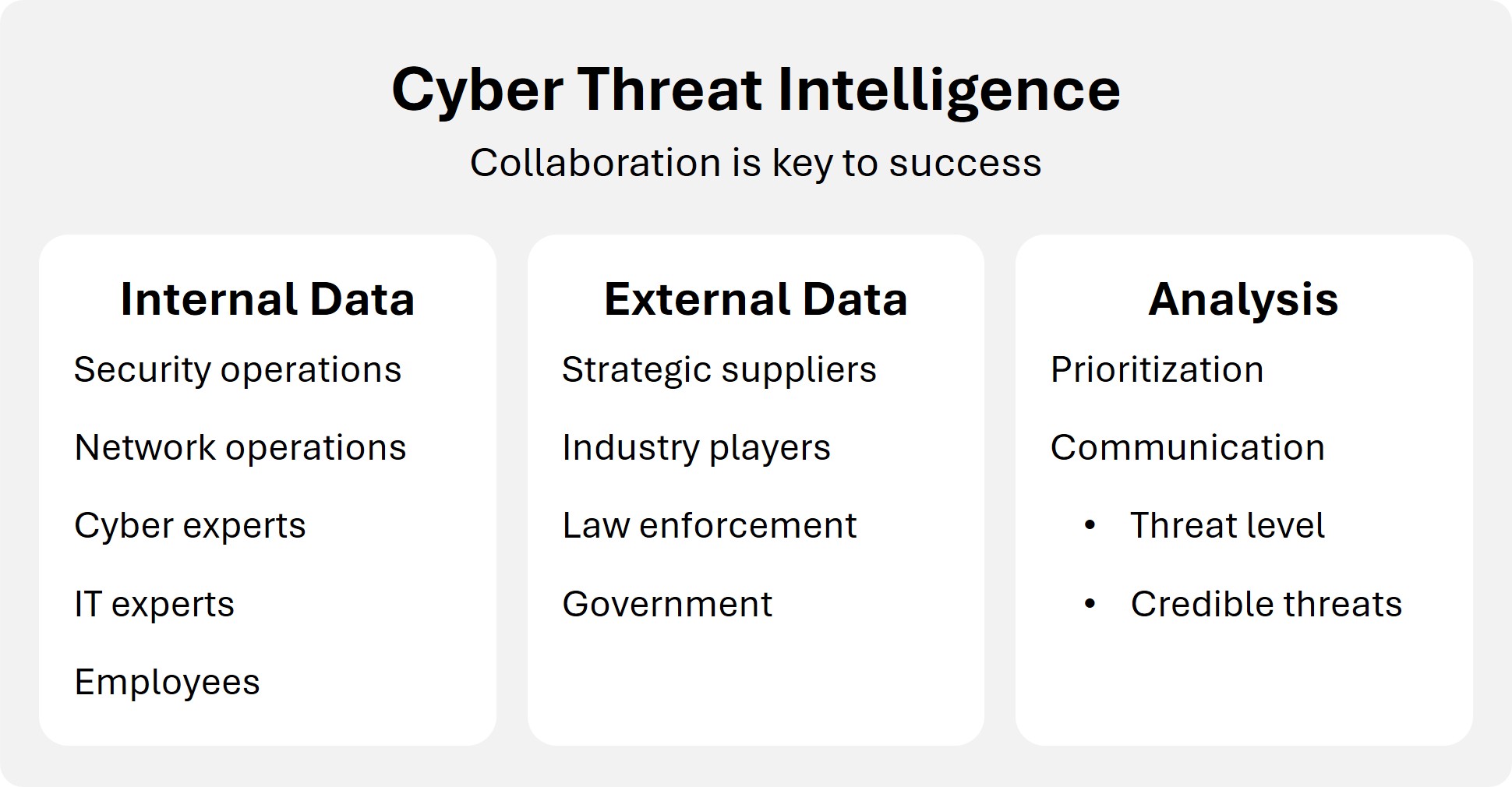
At the center is a Chief Information Security Officer with a team of security architects, operators, and cyber intelligence experts. This team must collaborate effectively with business and function leaders across the enterprise including IT, risk management, legal, and regulatory compliance, and corporate communications. Moreover, collaboration with third parties such as law enforcement, government, and strategic suppliers is also critical.
Cyber Risk Analysis and Prioritization
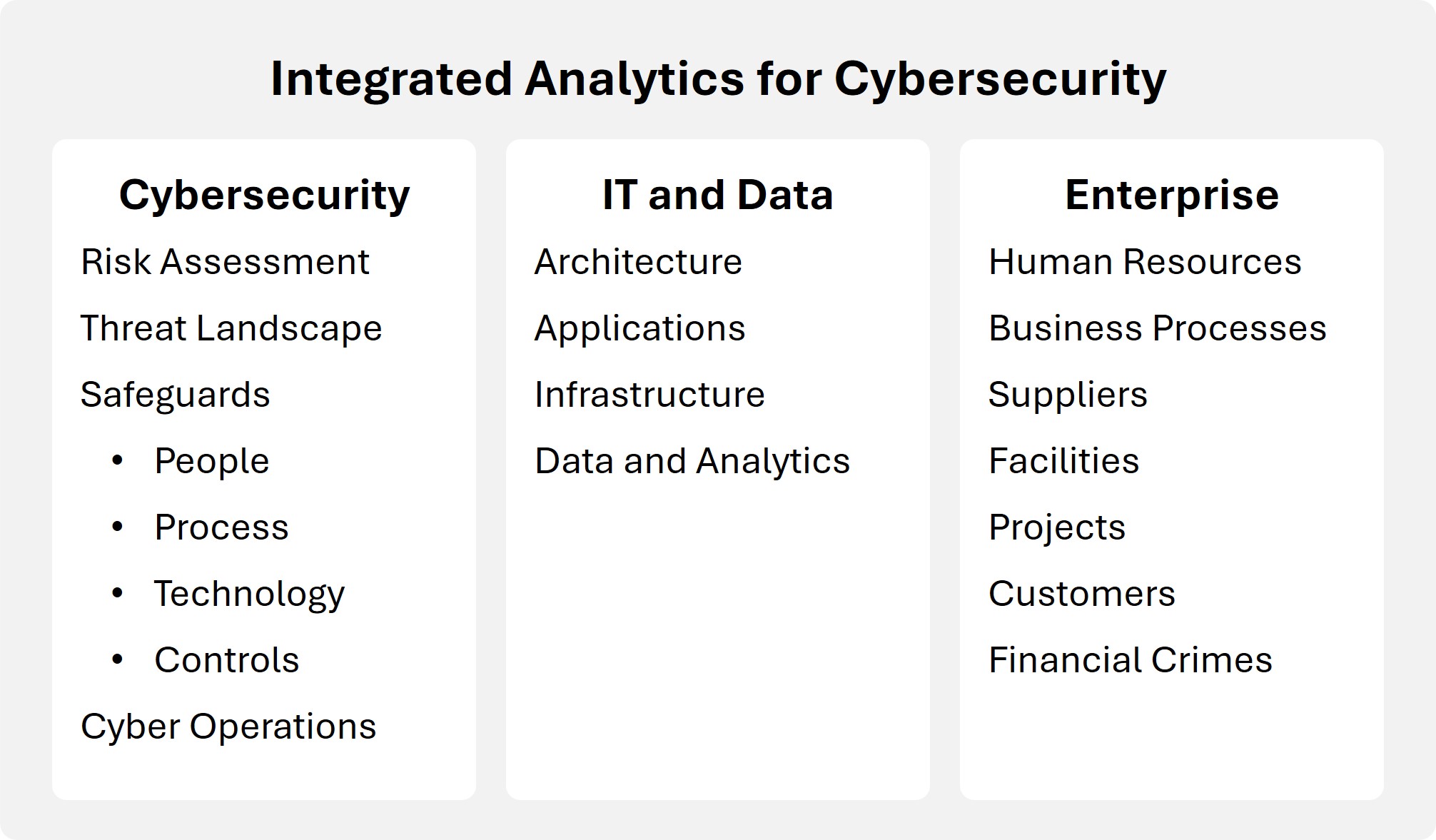
Enterprises do not have sufficient resources to protect all of their digital assets. Prioritization is therefore critical. This can be achieved with a risk assessment of business processes, enterprise applications, IT infrastructure, data, suppliers, facilities, projects. The NIST risk management framework (800-37) and zero trust architecture provide methodologies for control prioritization.
Cyber Controls Selection, Implementation, and Monitoring
Effective cybersecurity controls are critical to protecting your enterprise. NIST provides a catalog of over 250 cyber controls organized around 20 control families which illustrates the complexity of this problem. Cyber controls manifest themselves as software products and services. Selecting, implementing, and monitoring the effectiveness of cyber controls is vital to your success.

Security Operations
A cybersecurity operations center (SOC) typically monitors cyber threats and defensive activities across your enterprise. It can provide leaders and teams with valuable information on the evolution of cybersecurity threats and issues across your enterprise.
Threat Intelligence and Collaboration
Monitoring the external threat environment is critical. A team typically combines internal and external data sources to assess the threat landscape and credible threats to your enterprise. Your ability to understand this environment, be agile and take management actions if necessary is key to protecting your enterprise.
The Challenge: Complexity and Coordination
Managing cybersecurity effectively is challenging because it:
- Involves multiple stakeholders across the organization.
- Requires understanding and managing diverse types of risks.
- Needs continuous adaptation to evolving threats.
- Demands coordination between various teams and systems.
The Choral Advantage: Your Cyber Command Center
Understanding cybersecurity risk holistically and identifying critical issues quickly is crucial for effective risk management. But how can enterprises implement such capabilities rapidly?
Choral Systems has developed an innovative solution that addresses this challenge head-on.
Our approach combines advanced analytics solutions, a sophisticated data mesh, and a high-performance analytics platform. The result? Four transformational improvements in cybersecurity risk management:
1. Improved Collaboration
In today’s interconnected business environment, cross-functional collaboration is key to effective risk management. Our solution:
- Provides a “single pane of glass” view for all stakeholders
- Enables data-driven collaboration across departments
- Breaks down silos between cybersecurity, business units, and corporate functions
Benefits include:
- Unified perspective across the organization
- Timely decision-making based on integrated data
- Cross-domain insights that uncover hidden risks
- Transparent communication of goals and progress
- Empowered teams at all levels of the organization
- Streamlined, more productive meetings
2. Codified Expertise in Analytics Solutions
Our pre-built, customizable applications offer immediate value across various risk domains:
- Threat landscape analysis
- Cybersecurity risk assessment
- Controls monitoring
- Operations management
- Incident response
This integrated approach allows enterprises to:
- Gain a holistic view of cybersecurity risks
- Quickly focus on appropriate management actions
- Monitor execution of risk management initiatives
- Foster data-driven collaboration across departments
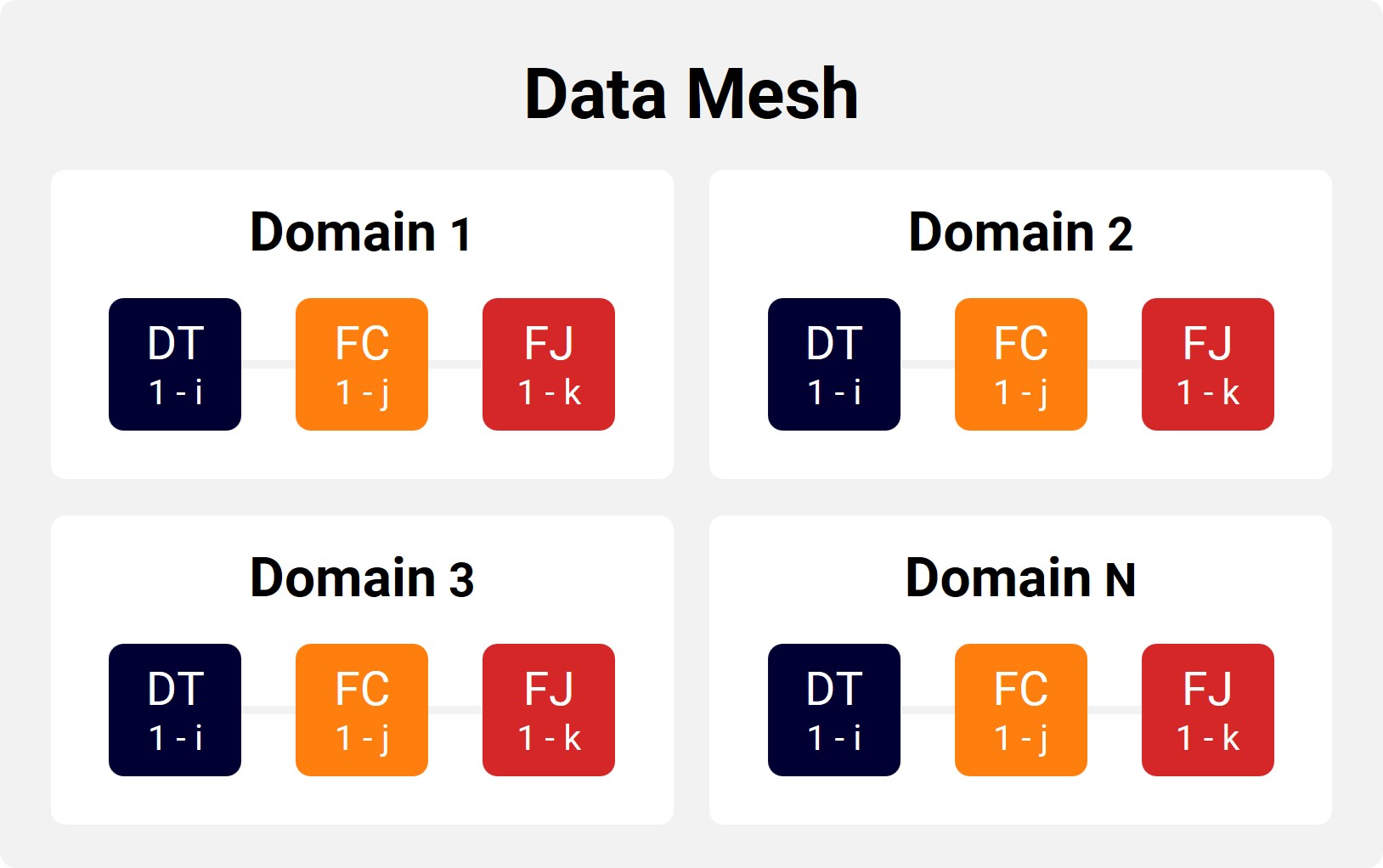
3. Organized and Connected Data
At the core of our solution is the Choral Data Mesh, a sophisticated data management architecture that:
- Organizes and interconnects structured and unstructured data from any source
- Serves as a common language between business leaders, functional leaders, and data teams
Key advantages include:
- Rapid data integration
- Cross-functional insights
- Seamless application integration
- Scalability and flexibility
- Empowered data ownership across the organization
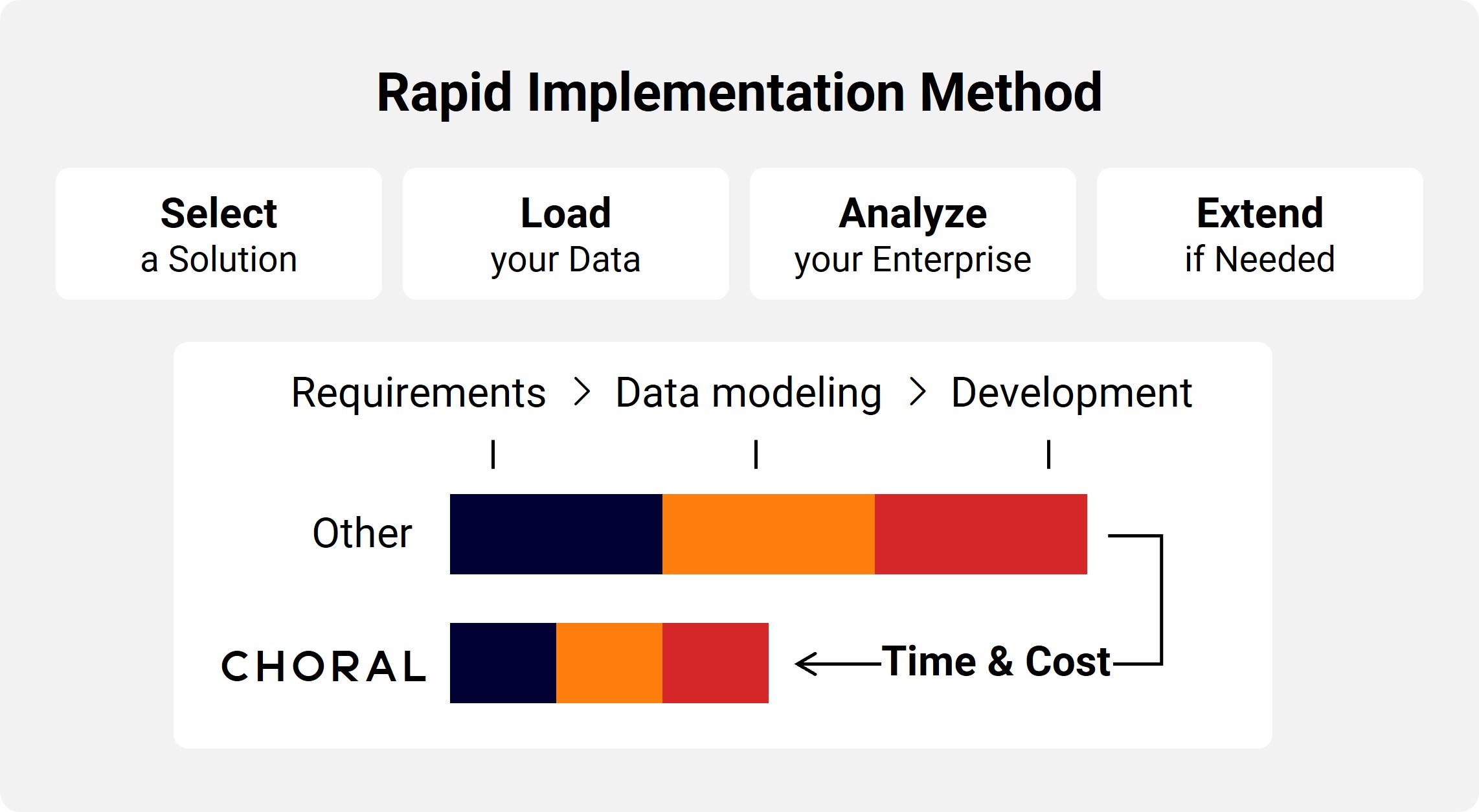
4. Rapid Implementation Method
Our unique methodology sets us apart, enabling:
- Deployment of solutions up to 10 times faster than traditional approaches
- Significant cost savings in implementation
This approach empowers you to:
- Improve cyber risk management with instant access to high-value data and analytics
- Enhance data-driven collaboration with a holistic view of cyber risks
- Quickly gain insights into issues requiring attention
- Stay agile in the face of rapidly evolving threats
By leveraging Choral’s integrated data and analytics approach, enterprises can transform raw data into actionable intelligence, responding to cybersecurity risks with unprecedented speed and precision.
Your Next Move
In this digital age, robust cybersecurity requires effective collaboration across your enterprise and with external stakeholders. With Choral, you’re not just defending against threats; you’re positioning your organization to be alert, informed and responsive.
Are you ready to take command of your cybersecurity strategy? Contact Choral Systems today and start your journey towards a more secure, resilient, and competitive future.
Remember, in the world of cybersecurity, knowledge isn’t just power – it’s your strongest defense.